In December, Oracle released the version 2.0.1 of the Database Security Assessment Tool (DBSAT) (German). One big enhancement is the introduction of the new Discoverer component, which can be used to identify sensitive data within your database.
This blog post will demonstrate how to configure and use the Discoverer.
Table of Contents
What is the Discoverer?
The Discoverer component is a Java-based utility (discoverer.jar) which identifies sensitive data by executing SQL queries primarily against the Data Dictionary. Which objects (schemas, tables, columns) the Discoverer marks as sensitive, depends on its configuration files. At the end a Database Sensitive Data Assessment Report is generated as HTML and CSV file.
You can run the Discoverer on the Database server or any other machine, e.g. your Laptop. To run the Discoverer you just need a Java Runtime Environment (JRE) 1.6 or higher.
Configuration
Before you execute the Discoverer, you have to configure it using a file called dbsat.config (any name can be used). A sample configuration can be found in the subdirectory Discover/conf.
$> cd Discover/conf $> cp sample_dbsat.config dbsat.config $> chmod u+w dbsat.config $> vi dbsat.config [Database] DB_HOSTNAME = localhost DB_PORT = 1521 DB_SERVICE_NAME = TESTDB [Discovery Parameters] SENSITIVE_PATTERN_FILES = sensitive_en.ini SCHEMAS_SCOPE = ALL MINROWS = 1 EXCLUSION_LIST_FILE = [Sensitive Categories] PII = High Risk PII - Address = High Risk PII - IDs = High Risk PII - IT Data = High Risk PII-Linked = Medium Risk PII-Linked - Birth Details = Medium Risk Job Data = Medium Risk Financial Data - PCI = High Risk Financial Data - Banking = Medium Risk Health Data = Medium Risk
It is mandatory to set at least the DB_SERVICE_NAME parameter. A connection using OS authentication is not possible.
Within this configuration file you configure the following properties.
- Database Connection
- Discovery Parameters
- Sensitive Categories
One important parameter is the SENSITIVE_PATTERN_FILES parameter within the Discovery Parameters group. This parameter contains a list of pattern files. These files define patterns – using regular expresssions – for identifying sensitive objects based on there name or description.
DBSAT delivers the pattern file sensitive_en.ini for the Englisch language, which contains 75 patterns for the following objects.
[AGE] [BANK_ACCOUNT_NUMBER] [BANK_NAME] [BANK_ROUTING_NUMBER] [BIRTHDATE] [BIRTHPLACE] [CARD_EXPIRATION_DATE] [CARD_SECURITY_CODE] [CARD_SECURITY_PIN] [CITY] [COOKIE] [COUNTRY_OF_CITIZENSHIP] [COUNTRY] [COUNTY] [CREDIT_CARD_NUMBER] [CRIMINAL] [DISABILITY] [DRIVERS_LICENSE_NUMBER] [EMAIL] [EMP_ID] [FATHERS_NAME] [FINGERPRINT] [FIRST_NAME] [FULL_ADDRESS] [FULL_NAME] [GENDER] [GENETIC] [HEALTH_INSURANCE_NUMBER] [HEIGHT] [HIRE_DATE] [IBAN] [IMEI] [INCOME] [IP_ADDRESS] [JOB_TITLE] [LAST_NAME] [LOCATION] [MAC_ADDRESS] [MAIDEN_NAME] [MAIL_STOP] [MARITAL_STATUS] [MEDICAL_CHART_NUMBER] [MEDICAL_INFORMATION] [MOTHERS_MAIDEN_NAME] [MOTHERS_NAME] [NATIONAL_IDENTIFIER] [NATIONAL_INSURANCE_NUMBER] [NATIONAL_TAXPAYER_IDENTIFIER] [NATIONALITY] [NEXT_OF_KIN] [PASSPORT_NUMBER] [PASSWORD] [PHONE] [PHOTO] [POLITICAL_PARTY] [POSTAL_CODE] [RACE] [RELIGION] [SEXUAL_PREFERENCE] [SOCIAL_INSURANCE_NUMBER] [SOCIAL_SECURITY_NUMBER] [STATE] [STOCK] [STREET] [STUDENT_IDENTIFICATION_NUMBER] [TAX_IDENTIFICATION_NUMBER] [TERMINATION_DATE] [TRADE_UNION_MEMBERSHIP] [UNIQUE_POPULATION_REGISTRY_CODE] [USERID] [VARIABLE_INCOME] [VISA_NUMBER] [VOTER_IDENTIFICATION_NUMBER] [WEIGHT] [WORK_PERMIT]
The following example will mark all objects belonging to credit card informations as sensitive data and map them to the “High Risk” category with the name Financial Data – PCI.
[CREDIT_CARD_NUMBER] COL_NAME_PATTERN = ^(?!.*(DATE|DT|ISSUE)).*(CREDIT|DEBIT).*CARD|^PAN$|PAYMENT_ACCT|^CCN?$|CC_CARD|CCI_N COL_COMMENT_PATTERN = (Credit|Debit|Payment) Card SENSITIVE_CATEGORY = Financial Data - PCI
If none of the existing patterns match, then you have to define them by your own.
For the case, that you want to exclude some objects (schemas, tables or columns), you can create a exclusion file and set it with EXCLUSION_LIST_FILE parameter.
<Schema>[.<Table>[.<Column>]]
For a complete overview of all parameters, check the User Guide of DBSAT.
Run Discoverer
After setting the environment for your target database, just run the dbsat utility using the created configuration file.
$> export JAVA_HOME=$ORACLE_HOME/jdk/jre
$> # Usage: ./dbsat discover -c <Path to Configfile> <Output File Name>
$> ./dbsat discover -c Discover/conf/dbsat.config testdb_data
Database Security Assessment Tool version 2.0.1 (December 2017)
This tool is intended to assist in you in securing your Oracle database
system. You are solely responsible for your system and the effect and
results of the execution of this tool (including, without limitation,
any damage or data loss). Further, the output generated by this tool may
include potentially sensitive system configuration data and information
that could be used by a skilled attacker to penetrate your system. You
are solely responsible for ensuring that the output of this tool,
including any generated reports, is handled in accordance with your
company's policies.
Enter username: system
Enter password:
DBSAT Discover ran successfully.
Calling /usr/bin/zip to encrypt the generated reports...
Enter password:
Verify password:
zip warning: testdb_data_report.zip not found or empty
adding: testdb_data_discover.html (deflated 76%)
adding: testdb_data_discover.csv (deflated 53%)
Zip completed successfully.
If you don’t want to encrypt the reports, add parameter -n.
Check Report
After the Discoverer finished his work, unzip the archive and verify the findings. By the way, the following report belongs to a database with all components installed, but without user objects and data.
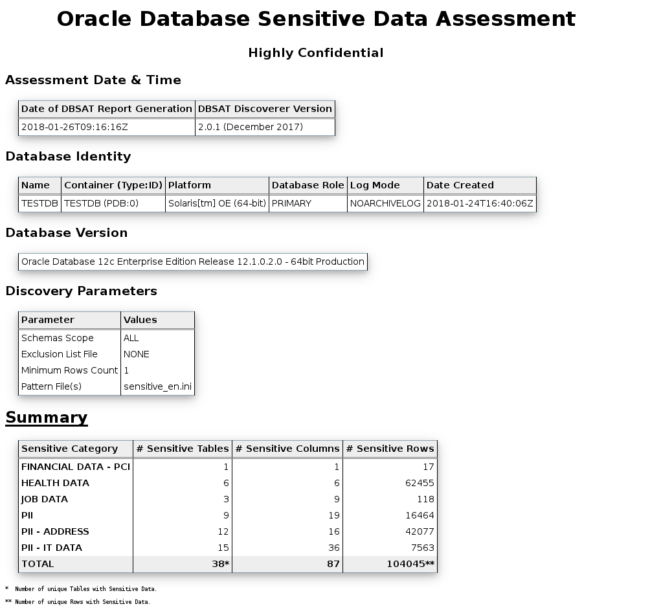
Note: The displayed rowcounts are derived from the object statistics – no access to these tables are performed. So it is recommended to have current statistics.
Example of tables with sensitive data.
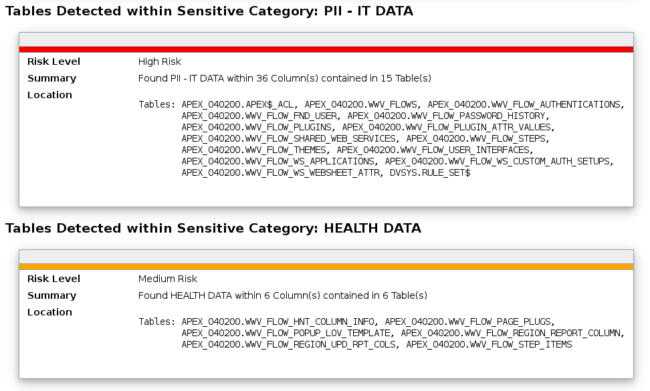
Conclusion
In times of GDPR and data thefts, it is mandatory to know which sensitive data is stored within your databases. To identify such risks, the new Discoverer component of DBSAT can be easily used to get a fast and good overview. And the best thing is, that the overhead to run this tool is not measurable.
